Simplify Your Path to Cyber Maturity Model Certification
Receive a CMMC gap analysis and readiness assessment conducted by a CMMC-AB Registered Practitioner. Our consultants will help you prepare for certification.
Expert Services For: HIPAA, CMMC, SOC 2, FTC Safeguards, ISO, HITRUST, NIST CSF, Cyber Insurance Applications, and MORE

Simplify Your Path to Cyber Maturity Model Certification
Receive a CMMC gap analysis and readiness assessment conducted by a CMMC-AB Registered Practitioner. Our consultants will help you prepare for certification.
Initial Readiness Assessment
Develop CMMC Roadmap
After the initial readiness assessment, our consultants will help you build your information security program to the desired CMMC compliance level.
Learn More
Re-Assess on a Quarterly Basis
We conduct benchmark assessments throughout the year to re-evaluate your gaps. This allows you to stay on target with your CMMC compliance goals.
Re-Assess on a Quarterly Basis
• Identify any new threats to your environment
• Meet your Cyber Maturity Model Certification goals
Free Security Risk Assessment
Gain an understanding of your current information security posture by completing this self-assessment. You will receive an S2SCORE estimate that will measure your controls and associated risks in your environment. This is completely free and confidential. Get started today!
Certified Experts
All Assessments are conducted by DueNorth Security staff members who hold at least one of the following certifications:

CMMC Readiness Assessment
If you are a contractor or subcontractor with the Department of Defense (DoD) that will be required to pass a CMMC Assessment, now is the time to start preparing. During your assessment, you will be required to prove that the security processes are “institutionalized” within your organization. Meaning, you must show that the correct security processes have been in place for a significant period of time. Now is the time for implementation!
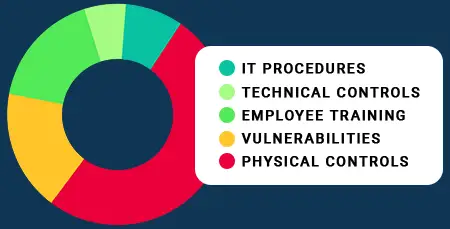
DueNorth uses an unbiased, quantifiable readiness assessment process to help you identify gaps. We can help with any remediation efforts including policy and procedure creation, employee training, vulnerability assessments, and more.
How can a CMMC assessment improve our bottom line ?
How long does a risk assessment take?
The basic assessment can be completed in 3 weeks while a more comprehensive assessment for organizations seeking Level 3-5 CMMC compliance can take up to 8 weeks.
What are the end deliverables?
All assessments include: CMMC Gap Analysis Report, NIST 800-171 report, a Security Risk Score, a CMMC Action Plan, Full Security Risk Assessment Report, Executive Summary with recommendations and all supporting documents and findings. DueNorth can also help with your remediation efforts.
Other Assessment Options:
Call Us

Let Us Know How We Can Help
Get More Information Today
"*" indicates required fields
Awesome Clients
What is the FTC Safeguards Rule
The FTC Safeguards Rule mandates that non-banking financial institutions, such as mortgage brokers, motor vehicle dealers, insurance provider, payday lenders and other businesses develop, implement, and maintain comprehensive information security programs. These...
NIST Cybersecurity Framework Risk Assessment Process
Cybersecurity for your business can be confusing. You want to protect your business from breaches, data theft, and ransomware. You also have a myriad of information security compliance requirements. Where should you put your time and money to try to be both secure...
The Importance of Business Impact Analysis
As the name signifies, a BIA quantifies the impact of a cyber disruption on your business. It doesn’t matter if the disruption happens because of an internet outage or a severe breach — a BIA covers it all. A business impact analysis lays the foundation for a strong...