Articles
Patching is not Vulnerability Management
While often used interchangeably, vulnerability management and patching are distinct, yet complementary, processes. Understanding their differences is crucial for a well-rounded security strategy. What Is Vulnerability Management? Vulnerability management is a...
Avoid a Fine, Align with a Recognized Security Practice
On January 5, 2021, the HIPAA Safe Harbor Law was enacted as Public Law 116-321. This law requires the U.S. Department of Health and Human Services (HHS) and OCR to consider whether a covered entity or business associate has “recognized security practices” in place...
How to Classify and Tag Confidential Information
Organizational confidential information is a vital asset that must be safeguarded to protect business integrity, compliance, and competitive advantage. For IT professionals, properly classifying and tagging this information is not only a technical requirement but also...
Security Risk For Healthcare Organizations
Understanding the Landscape of Cyber Threats in Healthcare Healthcare organizations face a myriad of cyber threats, including ransomware attacks, data breaches, and phishing schemes. The sensitive nature of health information makes it a prime target for...
What is the FTC Safeguards Rule
The FTC Safeguards Rule mandates that non-banking financial institutions, such as mortgage brokers, motor vehicle dealers, insurance provider, payday lenders and other businesses develop, implement, and maintain comprehensive information security programs. These...
NIST Cybersecurity Framework Risk Assessment
Cybersecurity for your business can be confusing. You want to protect your business from breaches, data theft, and ransomware. You also have a myriad of information security compliance requirements. Where should you put your time and money to try to be both secure...
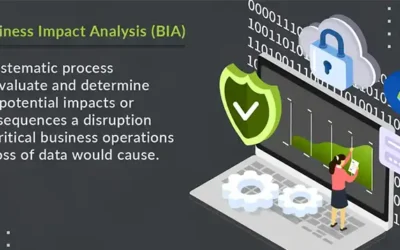
The Importance of Business Impact Analysis
As the name signifies, a BIA quantifies the impact of a cyber disruption on your business. It doesn’t matter if the disruption happens because of an internet outage or a severe breach — a BIA covers it all. A business impact analysis lays the foundation for a strong...
Protecting Personally Identifiable Information
Personally Identifiable Information (PII) refers to any information maintained by an agency that can be used to identify or trace a specific individual. In other words, it includes data points, such as social security number, date of birth, mother's maiden name,...
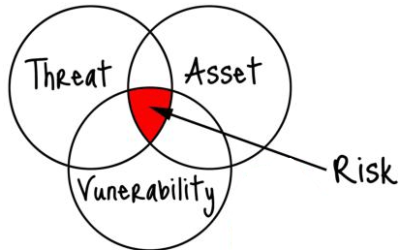
Ranking Information Security Risk
We have all seen the red, yellow, and green used on information security risk assessments to indicate high, medium, and low levels of risk. It is common with DIY security risk assessment tools used to satisfy HIPAA compliance. It’s time to retire this methodology....
Top 8 Security Risk Assessment Findings
We conduct dozens of security risk assessments for clients each year. It’s not surprising that we see a common pattern of issues among many of the organizations. Below is a description of these issues and what you can do to manage the risk associated with them. ...
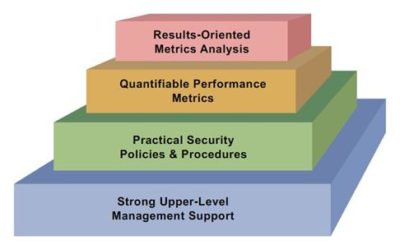
How to Build an Information Security Program
Executives and board members realize the importance of building a strong information security program. Current efforts to protect information are now subject to more scrutiny by their customers, insurance companies and the government. Ransomware and cyber-attacks...
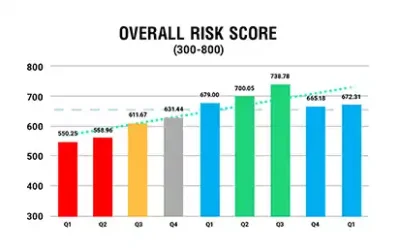
S2Score
S2Score is a comprehensive, risk-based measurement of information security assigned to your company based on a proven and thorough assessment process. Once completed, it will identify critical vulnerabilities, control gaps/ deficiencies, and applicable threats to the...
DueNorth Hires Brandon Haggerty, CISSP, GCWN
Brandon Haggerty, CISSP, GCWN Director of Security and Professional Services BA St John’s University MS Minnesota State University – Mankato DueNorth is pleased to announce that Brandon Haggerty, CISSP has joined NorthStar in a full-time capacity as of September 2018....
Avoid a Security Audit in Five Steps
The term “security audit” is often used synonymously with security risk assessment and risk analysis. But a security audit for HIPAA compliance is when Health and Human Services (HHS) audits a covered entity or business associate to determine their level of compliance...
4 Types of Information Security Threats
No matter how long you have been dealing with HIPAA there are probably some parts you just don’t get. In the end, the HIPAA Security Rule exists to prevent bad stuff from happening. So what is your risk of bad stuff happening? That’s the purpose of one of the HIPAA...
Call Us

Let Us Know How We Can Help
Get More Information Today
"*" indicates required fields