Executives and board members realize the importance of building a strong information security program. Current efforts to protect information are now subject to more scrutiny by their customers, insurance companies and the government. Ransomware and cyber-attacks have elevated global awareness of what makes for a solid information security “program.”
But in fact, a “program” is exactly what makes information security efforts ineffective. A program is too often understood as a siloed effort within an organization that falls under the responsibilities of a team or department. Organizations need to understand that information security must be part of their culture.
Information security’s evolution parallels physical security at schools over the past decade. Schools don’t have a student protection “program.” Protecting the students is priority #1. It’s not an inconvenient set of policies and procedures that can be skirted when the workload gets too heavy. It’s part of every workday and part of their culture.
As a matter of fact, any security framework considers human protection as the first objective. In healthcare, the protection of patient information IS a matter of protecting human life. If health information is altered, misplaced, or destroyed and can lead to misdiagnoses and mistreatment. So now that we understand that the information we create, store and transmit is important enough to protect, how do we do it right.
The first thing to understand is that technology doesn’t protect information, people protect information…. And not just your IT people, everyone.
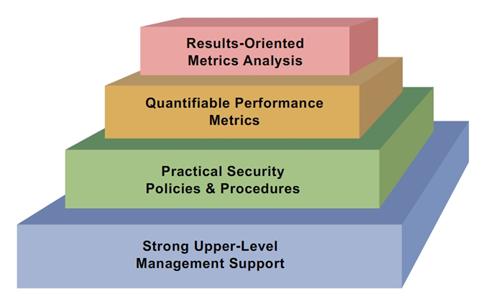
A solid framework helps to manage information security. The S2Score offers a great metrics model to get you started.
-
-
-
Step # 1 – Strong upper management support is critical to the implementation and the success of the information security program.
-
-
A strong commitment to information security within the highest levels of the management of an organization helps to protect the security program from organizational pressures and budget limitations.
-
-
-
Step # 2 – Information security policies and procedures that are enforced and backed by management are essential for an effective information security measurement program.
-
-
Information security policies delineate the information security management structure, assign information security responsibilities, and lay the foundation needed to reliably measure progress and compliance. These policies and procedures help to assure that data is available and can be used for measurement processes.
-
-
-
Step #3 – Quantifiable performance measures are necessary in order to capture and provide meaningful performance data.
-
-
Quantifiable information security measures must be based on information security performance goals and objectives, and must be easily obtainable, feasible to measure, and repeatable. The information provided should demonstrate performance trends and facilitate decisions for future resource investments.
-
-
-
Step # 4 – Periodic results-oriented analysis of the measures data must be a consistent part of the information security measurement program.
-
-
The analyses are used to apply lessons learned, improve the effectiveness of existing security controls, and plan for the implementation of future security controls to meet emerging information security requirements. All stakeholders and users must be committed to the accurate collection of data that is meaningful and useful in improving the overall information security program.
We would be happy to discuss how your organization can get started. Please call or write anytime.