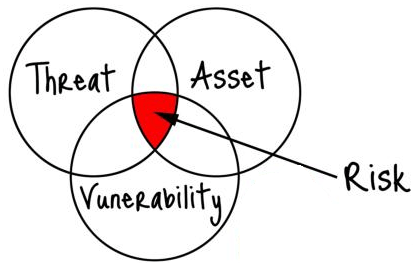
We conduct dozens of security risk assessments for clients each year. It’s not surprising that we see a common pattern of issues among many of the organizations. Below is a description of these issues and what you can do to manage the risk associated with them. These common issues (vulnerabilities) made the list because they have a high likelihood of being exploited by a threat and compromising an asset. Information security can be complex topic but solving these basic issues is not difficult if you understand what you are trying to manage.
Common issues:
- Not conducting a security risk assessment. You can’t protect your information if you don’t know:
- What you are trying to protect
- What are the threats to it
- What are your vulnerabilities to those threats
- Untrained employees. Information security is not a technology problem, it’s a people problem. Training employees on common threats like email phishing scams and password protection is the biggest thing that organizations can do.
- Sending and storing protected information without using encryption. This applies to sending unencrypted email and not have encryption on laptops. This is typically a matter of determining what information you want to protect and to develop encryption solutions around that information.
- Anti-virus or security patches missing. It seems simple, right? This needs to be managed constantly.
- Not having a security officer. The buck needs to stop somewhere. A security officer doesn’t need to be the most technical person within your organization. They do need to have the authority to make organizational-wide decisions on how information is used. The security officer should not be part of the IT department.
- Unmanaged employee access. This applies to things like folder shares, cloud services, email distribution groups. 75% of security breaches are caused by internal threats. Organizations need to know who has access to what by reviewing lists regularly.
- Unmanaged VPN accounts. This could tie into #6 if an employee has a vpn account but also applies to vendors and partners. A security officer should be reviewing a list of vpn accounts regularly to determine if they are necessary and that the settings match the protocols determined by the organization.
- Unmanaged file sync/share programs. Things like dropbox, google docs, one drive can be setup by an employee and easily be used to store or share protected information. Whether there is malicious intent or not, these programs need to be managed and controlled.
You don’t need your masters in information systems to manage information security. You need to understand basic risks and ask a lot of questions. It all starts with a well-organized and thorough information security assessment.