
by markschlader | Apr 22, 2024 | Front Page, Uncategorized
The FTC Safeguards Rule mandates that non-banking financial institutions, such as mortgage brokers, motor vehicle dealers, insurance provider, payday lenders and other businesses develop, implement, and maintain comprehensive information security programs. These...
by markschlader | Aug 19, 2022 | Front Page, Uncategorized
As the name signifies, a BIA quantifies the impact of a cyber disruption on your business. It doesn’t matter if the disruption happens because of an internet outage or a severe breach — a BIA covers it all. A business impact analysis lays the foundation for a strong...
by markschlader | Aug 4, 2021 | Uncategorized
Personally Identifiable Information (PII) refers to any information maintained by an agency that can be used to identify or trace a specific individual. In other words, it includes data points, such as social security number, date of birth, mother’s maiden name,...
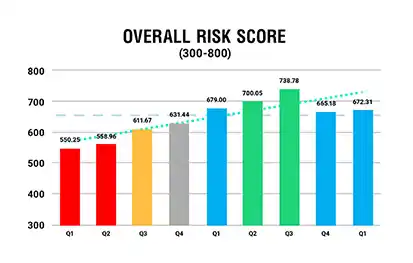
by markschlader | Nov 17, 2020 | Uncategorized
We have all seen the red, yellow, and green used on information security risk assessments to indicate high, medium, and low levels of risk. It is common with DIY security risk assessment tools used to satisfy HIPAA compliance. It’s time to retire this methodology....
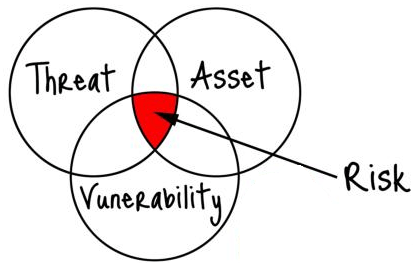
by markschlader | May 28, 2019 | Uncategorized
We conduct dozens of security risk assessments for clients each year. It’s not surprising that we see a common pattern of issues among many of the organizations. Below is a description of these issues and what you can do to manage the risk associated with them. ...

by markschlader | Mar 25, 2019 | Uncategorized
S2Score is a comprehensive, risk-based measurement of information security assigned to your company based on a proven and thorough assessment process. Once completed, it will identify critical vulnerabilities, control gaps/ deficiencies, and applicable threats to the...







Recent Comments