
by markschlader | Apr 22, 2024 | Front Page, Uncategorized
The FTC Safeguards Rule mandates that non-banking financial institutions, such as mortgage brokers, motor vehicle dealers, insurance provider, payday lenders and other businesses develop, implement, and maintain comprehensive information security programs. These...

by Mike Rezl | Feb 23, 2024 | Front Page
Cybersecurity for your business can be confusing. You want to protect your business from breaches, data theft, and ransomware. You also have a myriad of information security compliance requirements. Where should you put your time and money to try to be both secure...
by markschlader | Aug 19, 2022 | Front Page, Uncategorized
As the name signifies, a BIA quantifies the impact of a cyber disruption on your business. It doesn’t matter if the disruption happens because of an internet outage or a severe breach — a BIA covers it all. A business impact analysis lays the foundation for a strong...
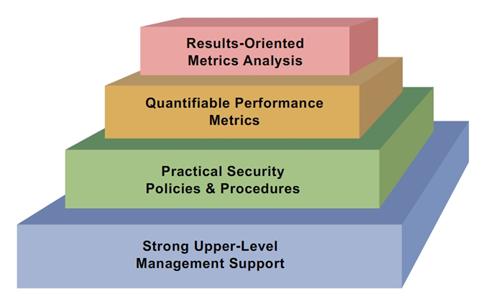
by markschlader | Apr 3, 2019 | Front Page
Executives and board members realize the importance of building a strong information security program. Current efforts to protect information are now subject to more scrutiny by their customers, insurance companies and the government. Ransomware and cyber-attacks...

by markschlader | Oct 4, 2018 | Front Page
The term “security audit” is often used synonymously with security risk assessment and risk analysis. But a security audit for HIPAA compliance is when Health and Human Services (HHS) audits a covered entity or business associate to determine their level of compliance...







Recent Comments